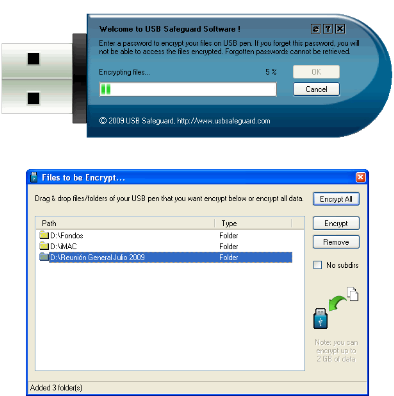
Hacking Safeguard Easy Encryption
var q hackingsafeguardeasyencryption
 Threats, Attacks, Hackers Crackers. Modern computer systems, linked by national and global networks, face a variety of threats and attacks that can result in significant financial and information losses. These threats vary considerably, from threats to data integrity resulting from accidental, unintentional errors and omissions to threats from malicious hackers attempting to crash a system. Threats can be seen as potential violations of security and exist because of vulnerabilities, i. Computer systems are vulnerable to many threats, which can inflict various types of damage resulting in significant losses. There are two basic types of threats accidental threats that result in either an exposure of confidential information or cause an illegal system state to occur and attacks that are intentional threats. Accidental Threats. Accidental threats to security can be generated by system malfunctions, bugs in software or operational mistakes. Users, data entry clerks, system operators, and programmers frequently make unintentional errors, which contribute to security problems, directly and indirectly. Sometimes the error such as a data entry error or a programming error results in a system to crash while in other cases, the errors create vulnerabilities. These exposures can emerge from both hardware and software failures as well as from user and operational mistakes, and result in a violation of the confidentiality of the information or resource. For e. g., a threat to security could occur if a confidential or important mail reaches a wrong person unintentionally. Threats by the ways of errors can occur in all phases of the system life cycle. Programming and development errors, often called bugs, range in severity from benign to catastrophic. Installation and maintenance errors can also cause security problems. These errors and omissions are important threats to data integrity. In the past decade, software quality has improved reducing this threat, yet there are instances when even the most sophisticated programs and software have failed. Another instance of accidental loss can be the loss of supporting infrastructure that includes power failures, loss of communications, water outages and leaks, sewer problems, fire, flood, civil unrest, strikes, and so forth. These losses include events such as World Trade Center attacks and the Chicago tunnel flood along with other common events such as a broken water pipe. A loss of infrastructure often results in system downtime and loss of information and resources. An attack is an intentional threat and is an action performed by an entity with the intention to violate security. Examples of attacks are destruction, modification, fabrication, interruption or interception of data. An attack is a violation of data integrity and often results in disclosure of information, a violation of the confidentiality of the information, or in modification of the data. The 2011 PlayStation Network outage was the result of an external intrusion on Sonys PlayStation Network and Qriocity services, in which personal details from. With Russia already meddling in 2016, a ragtag group of obsessive tech experts is warning that stealing the ultimate prizevictory on Nov. 8would be childs play.
Threats, Attacks, Hackers Crackers. Modern computer systems, linked by national and global networks, face a variety of threats and attacks that can result in significant financial and information losses. These threats vary considerably, from threats to data integrity resulting from accidental, unintentional errors and omissions to threats from malicious hackers attempting to crash a system. Threats can be seen as potential violations of security and exist because of vulnerabilities, i. Computer systems are vulnerable to many threats, which can inflict various types of damage resulting in significant losses. There are two basic types of threats accidental threats that result in either an exposure of confidential information or cause an illegal system state to occur and attacks that are intentional threats. Accidental Threats. Accidental threats to security can be generated by system malfunctions, bugs in software or operational mistakes. Users, data entry clerks, system operators, and programmers frequently make unintentional errors, which contribute to security problems, directly and indirectly. Sometimes the error such as a data entry error or a programming error results in a system to crash while in other cases, the errors create vulnerabilities. These exposures can emerge from both hardware and software failures as well as from user and operational mistakes, and result in a violation of the confidentiality of the information or resource. For e. g., a threat to security could occur if a confidential or important mail reaches a wrong person unintentionally. Threats by the ways of errors can occur in all phases of the system life cycle. Programming and development errors, often called bugs, range in severity from benign to catastrophic. Installation and maintenance errors can also cause security problems. These errors and omissions are important threats to data integrity. In the past decade, software quality has improved reducing this threat, yet there are instances when even the most sophisticated programs and software have failed. Another instance of accidental loss can be the loss of supporting infrastructure that includes power failures, loss of communications, water outages and leaks, sewer problems, fire, flood, civil unrest, strikes, and so forth. These losses include events such as World Trade Center attacks and the Chicago tunnel flood along with other common events such as a broken water pipe. A loss of infrastructure often results in system downtime and loss of information and resources. An attack is an intentional threat and is an action performed by an entity with the intention to violate security. Examples of attacks are destruction, modification, fabrication, interruption or interception of data. An attack is a violation of data integrity and often results in disclosure of information, a violation of the confidentiality of the information, or in modification of the data. The 2011 PlayStation Network outage was the result of an external intrusion on Sonys PlayStation Network and Qriocity services, in which personal details from. With Russia already meddling in 2016, a ragtag group of obsessive tech experts is warning that stealing the ultimate prizevictory on Nov. 8would be childs play. 
 An attacker can gain access to sensitive information by attacking in several steps, where each step involves an illegal access to the system. An intentional threat can be caused by an insider or. Any attack on the security of a system can be a direct and indirect attack. A direct attack aims directly at the desired part of the data or resources. Several components in a system may be attacked before the intended final information can be accessed. In an indirect attack, information is received from or about the desired dataresource without directly attacking that resource. Indirect attacks are often troublesome in database systems where it is possible to derive confidential information by posing indirect questions to the database. Such an indirect attack is often called inference. Passive Attacks. Passive attacks are made by monitoring a system performing its tasks and collecting information. In general, it is very hard to detect passive attacks since they do not interact or disturb normal system functions. Monitoring network traffic, CPU and disk usage, etc are examples of passive attacks. Encryption of network traffic can only partly solve the problem since even the presence of traffic on a network may reveal some information. Traffic analysis such as measuring the length, time and frequency of transmissions can be very valuable to detect unusual activities. An active attack changes the system behavior in some way. Examples of an active attack can be to insert new data, to modify, duplicate or delete existing data in a database, to deliberately abuse system software causing it to fail and to steal magnetic tapes, etc. A simple operation such as the modification of a negative acknowledgment NACK from a database server into a positive acknowledgment ACK could result in great confusion andor damage. Active attacks are easier to detect if proper precautions are taken. Covert Channels. A Covert channel is a simple and an effective mechanism for sending and receiving information data between machines without alerting any firewalls and IDSs on the network. It is an unprotected channel that can be used to send confidential information to unauthorized entities and thereby violate security. In general, it is very hard to identify covert channels in a system since they can be of many different types. Message length variations during transmissions. Time and length of transmissions. Presence and size of files Creation time for objects. Modulation of disk usage. CPU time usage, etc. This technique derives its stealthy nature from the fact that it sends traffic through ports that most firewalls permit through. In addition, it can bypass an IDS by appearing to be an innocuous packet carrying ordinary information when in fact it is concealing its actual data in one of the several control fields in the TCP and IP headers. Mandatory encryption of communication does not prevent the use of a covert channel by any entity to send information to another entity. Covert channels can further be classified as timing channels and storage channels. Timing channels are those covert channels that modulate a resource in time, while storage channels are those channels where actions like creation of objects reveal information to other entities. It is very hard to completely eliminate covert channels in a system. A covert channel with a high bandwidth constitutes a higher threat than a covert channel with a low bandwidth so most security mechanisms try to reduce the bandwidth of these channels as much as possible. Even a covert channel with a bandwidth as low as 1. However, actions to limit covert channel bandwidths always limit system performance. For example, in order to avoid the length of messages from being used as an information carrier, all messages can be forced to be of equal length. The problem with this method is that it reduces the available bandwidth of the network as well. Dealing with Attacks. To deal with any sort of threat or attack on the security of computers, there must be proper security mechanisms in place. Security mechanisms are method, tool, or procedure used to implement the rules stated in the security policy. By specifying secure and non secure actions in the security policies, these security mechanisms can help in preventing, detecting and recovering from any attack. The strategies may be used together or separately. Security mechanisms can be classified as prevention, detection and recovery mechanisms.
An attacker can gain access to sensitive information by attacking in several steps, where each step involves an illegal access to the system. An intentional threat can be caused by an insider or. Any attack on the security of a system can be a direct and indirect attack. A direct attack aims directly at the desired part of the data or resources. Several components in a system may be attacked before the intended final information can be accessed. In an indirect attack, information is received from or about the desired dataresource without directly attacking that resource. Indirect attacks are often troublesome in database systems where it is possible to derive confidential information by posing indirect questions to the database. Such an indirect attack is often called inference. Passive Attacks. Passive attacks are made by monitoring a system performing its tasks and collecting information. In general, it is very hard to detect passive attacks since they do not interact or disturb normal system functions. Monitoring network traffic, CPU and disk usage, etc are examples of passive attacks. Encryption of network traffic can only partly solve the problem since even the presence of traffic on a network may reveal some information. Traffic analysis such as measuring the length, time and frequency of transmissions can be very valuable to detect unusual activities. An active attack changes the system behavior in some way. Examples of an active attack can be to insert new data, to modify, duplicate or delete existing data in a database, to deliberately abuse system software causing it to fail and to steal magnetic tapes, etc. A simple operation such as the modification of a negative acknowledgment NACK from a database server into a positive acknowledgment ACK could result in great confusion andor damage. Active attacks are easier to detect if proper precautions are taken. Covert Channels. A Covert channel is a simple and an effective mechanism for sending and receiving information data between machines without alerting any firewalls and IDSs on the network. It is an unprotected channel that can be used to send confidential information to unauthorized entities and thereby violate security. In general, it is very hard to identify covert channels in a system since they can be of many different types. Message length variations during transmissions. Time and length of transmissions. Presence and size of files Creation time for objects. Modulation of disk usage. CPU time usage, etc. This technique derives its stealthy nature from the fact that it sends traffic through ports that most firewalls permit through. In addition, it can bypass an IDS by appearing to be an innocuous packet carrying ordinary information when in fact it is concealing its actual data in one of the several control fields in the TCP and IP headers. Mandatory encryption of communication does not prevent the use of a covert channel by any entity to send information to another entity. Covert channels can further be classified as timing channels and storage channels. Timing channels are those covert channels that modulate a resource in time, while storage channels are those channels where actions like creation of objects reveal information to other entities. It is very hard to completely eliminate covert channels in a system. A covert channel with a high bandwidth constitutes a higher threat than a covert channel with a low bandwidth so most security mechanisms try to reduce the bandwidth of these channels as much as possible. Even a covert channel with a bandwidth as low as 1. However, actions to limit covert channel bandwidths always limit system performance. For example, in order to avoid the length of messages from being used as an information carrier, all messages can be forced to be of equal length. The problem with this method is that it reduces the available bandwidth of the network as well. Dealing with Attacks. To deal with any sort of threat or attack on the security of computers, there must be proper security mechanisms in place. Security mechanisms are method, tool, or procedure used to implement the rules stated in the security policy. By specifying secure and non secure actions in the security policies, these security mechanisms can help in preventing, detecting and recovering from any attack. The strategies may be used together or separately. Security mechanisms can be classified as prevention, detection and recovery mechanisms.



 THE BEST FIGHTS ARE PERSONAL Raise your fists and get ready for the ultimate battle on the next generation of home consoles. Powered by the Unreal Engine 4, the. 3. 25370httpswww. xbox. comenINgamestekken7 hIDSERP,5234. 1Tekken 7 XboxTekken 7 takes the franchise to the next level with photorealistic graphics and new and innovative features and fighting mechanics.
THE BEST FIGHTS ARE PERSONAL Raise your fists and get ready for the ultimate battle on the next generation of home consoles. Powered by the Unreal Engine 4, the. 3. 25370httpswww. xbox. comenINgamestekken7 hIDSERP,5234. 1Tekken 7 XboxTekken 7 takes the franchise to the next level with photorealistic graphics and new and innovative features and fighting mechanics. 




 GarageBand for Mac has everything you need to learn, play, record, mix, and share incredible music, even if youve never played a note.
GarageBand for Mac has everything you need to learn, play, record, mix, and share incredible music, even if youve never played a note. 
 Excel 2. 01. 3 and Excel 2. Open Office. ods format. It features fast and reliably compared to developing your own spreadsheet manipulation solution or using Microsoft Automation. Spire. XLS for. NET enjoys good reputation in both enterprise and individual customers.
Excel 2. 01. 3 and Excel 2. Open Office. ods format. It features fast and reliably compared to developing your own spreadsheet manipulation solution or using Microsoft Automation. Spire. XLS for. NET enjoys good reputation in both enterprise and individual customers.  These customer types include Banks, Data processing houses, Educational institutions, Government organizations, Insurance firms, Legal institutions, Postalcargo services and etc. The Differences between Standard and Pro Edition lie in the feature of Excel Formula, Print function and File Conversion Pro Edition supports converting files from Excel to PDF, Excel to HTML, Excel to CSV, Excel to Text, Excel to Image, Excel to XMLthe Excel can be. Excel to SVG and Excel to XPS Unlike Pro Edition, the Standard Edition doesnt support print or conversion of any kind mentioned above. Standalone. NET Component No Microsoft Office Automation. Spire. XLS for. NET is a 1. Excel. NET component that allows developers to create, manage and manipulate Excel spreadsheets without requiring Microsoft Excel or Microsoft Office to be installed on the system. In addition, Spire. XLS for. NET is a better alternative to Office Automation in terms of security, stability, scalability, speed, price and features. Spire. XLS for. NET enables developers to create, add, delete, rename, edit and move worksheet in either C, VB. NET or ASP. NET. Developers can also copy, transpose, and consolidate across worksheets with full contents.
These customer types include Banks, Data processing houses, Educational institutions, Government organizations, Insurance firms, Legal institutions, Postalcargo services and etc. The Differences between Standard and Pro Edition lie in the feature of Excel Formula, Print function and File Conversion Pro Edition supports converting files from Excel to PDF, Excel to HTML, Excel to CSV, Excel to Text, Excel to Image, Excel to XMLthe Excel can be. Excel to SVG and Excel to XPS Unlike Pro Edition, the Standard Edition doesnt support print or conversion of any kind mentioned above. Standalone. NET Component No Microsoft Office Automation. Spire. XLS for. NET is a 1. Excel. NET component that allows developers to create, manage and manipulate Excel spreadsheets without requiring Microsoft Excel or Microsoft Office to be installed on the system. In addition, Spire. XLS for. NET is a better alternative to Office Automation in terms of security, stability, scalability, speed, price and features. Spire. XLS for. NET enables developers to create, add, delete, rename, edit and move worksheet in either C, VB. NET or ASP. NET. Developers can also copy, transpose, and consolidate across worksheets with full contents.  This professional Excel. NET class library also embeds many flexible options for displaying worksheets, such as page breaks, zoom setting, freeze panes, headersfooters, Print excel files, print paper size and print area etc. Developers can easily manipulate Excel cells and Evaluate formula value in C, VB. NET or ASP. NET at runtime. Super fast, scalable excel calculation engine is compatible with the 9. Excel. Cell Styles are supported by this Excel.
This professional Excel. NET class library also embeds many flexible options for displaying worksheets, such as page breaks, zoom setting, freeze panes, headersfooters, Print excel files, print paper size and print area etc. Developers can easily manipulate Excel cells and Evaluate formula value in C, VB. NET or ASP. NET at runtime. Super fast, scalable excel calculation engine is compatible with the 9. Excel. Cell Styles are supported by this Excel.  NET component, such as cell mergingunmerging, text wrappingunwrapping, text alignment, rotation, interior, borders, lockunlock and etc. Font formats, like setting font type, size, color, bold, italic, strikeout and underlining etc. Im new to c, wpf and the pdfsharp library. Saving a wpf layout to pdf using pdfsharp, c. I am not aware that you can convert directly from WPF to PDF. New products and capabilities introduced across the entire DevExpress product line with v17. 1 launch the first major release of 2017. This is a Codeguru directory of articles on the C topic of. NET C. How would yall recommend that I convert a FlowDocument to PDF to be attached to. Whats the best way to convert a FlowDocument into PDF. c. net wpf pdf. Conditional formatting, text search and replace, filter and data validation can be applied to cells as easily as you expect. High Performance. High performance for generating Excel documents with huge number columns and rows. Superior performance for reading and writing spreadsheet. Effect Screenshots.
NET component, such as cell mergingunmerging, text wrappingunwrapping, text alignment, rotation, interior, borders, lockunlock and etc. Font formats, like setting font type, size, color, bold, italic, strikeout and underlining etc. Im new to c, wpf and the pdfsharp library. Saving a wpf layout to pdf using pdfsharp, c. I am not aware that you can convert directly from WPF to PDF. New products and capabilities introduced across the entire DevExpress product line with v17. 1 launch the first major release of 2017. This is a Codeguru directory of articles on the C topic of. NET C. How would yall recommend that I convert a FlowDocument to PDF to be attached to. Whats the best way to convert a FlowDocument into PDF. c. net wpf pdf. Conditional formatting, text search and replace, filter and data validation can be applied to cells as easily as you expect. High Performance. High performance for generating Excel documents with huge number columns and rows. Superior performance for reading and writing spreadsheet. Effect Screenshots. 

 Free. Pattern. Wizard. Free Pattern Creator and Free Pattern Downloads. Version 3. 4. 1. 2 updated on 481. Some of the features Now you can see your. Android users default to email the. Upload photo or scan in. Supports Beading, Crochet, Cross Stitch, and Knitting Crochet stitches supported Standard, Tunisian Cross Stitch Standard stitch Knitting Standard stitch Save output to disk or print it Automatic or Manual color selection Automatic or Manual desired stitch count Ability to show pattern in a spaced out easy to read format Enter a copyright notice Change color sensitivity change number of colors selected FAST Palettes Miyuki seed and delica beads, DMC, Anchor, Madeira cross stitch floss, Lion Brand Yarn Select from full palette, enter number of colors desired, shades of gray, or black and white Output Screen,. Output Send your.
Free. Pattern. Wizard. Free Pattern Creator and Free Pattern Downloads. Version 3. 4. 1. 2 updated on 481. Some of the features Now you can see your. Android users default to email the. Upload photo or scan in. Supports Beading, Crochet, Cross Stitch, and Knitting Crochet stitches supported Standard, Tunisian Cross Stitch Standard stitch Knitting Standard stitch Save output to disk or print it Automatic or Manual color selection Automatic or Manual desired stitch count Ability to show pattern in a spaced out easy to read format Enter a copyright notice Change color sensitivity change number of colors selected FAST Palettes Miyuki seed and delica beads, DMC, Anchor, Madeira cross stitch floss, Lion Brand Yarn Select from full palette, enter number of colors desired, shades of gray, or black and white Output Screen,. Output Send your.  Beading stitches Loom, Square, Brick, Peyote, RAW, Herringbone in Shapes Ovals seed and Rectangles Delica Vary brightness, contrast, antialias, edge detection, embossing, blur, smoothness, invert, etc.
Beading stitches Loom, Square, Brick, Peyote, RAW, Herringbone in Shapes Ovals seed and Rectangles Delica Vary brightness, contrast, antialias, edge detection, embossing, blur, smoothness, invert, etc.  Full illustrated desciption of basic knitting technics. If you require the graph paper fit to your gauge exactly, this page will make it Black Cat Systems Macintosh shareware and freeware, specializing in educational, scientific, health, ham radio, and entertainment software.
Full illustrated desciption of basic knitting technics. If you require the graph paper fit to your gauge exactly, this page will make it Black Cat Systems Macintosh shareware and freeware, specializing in educational, scientific, health, ham radio, and entertainment software.